The Difference is Clear!
• Local Service
• Fast Response Times
• Complete IT Service
• One number to call
• Clear Service Level Agreements
• Extensive Experience
• Proactive Service
• Regular Check-ups
• Remote monitoring of system
'. First Choice Computers .' '..... Total piece of mind ....' '... Your already infected ...' ' "Have you got a backup" ' Do not open attachments from recipients that you don't recognise. And remember HMRC, Amazon, British Banks and many other named institutions do not send email attachments. Spread the word!

Contact: info@cc-online.co.uk

Cryptolocker thieves likely making 'Millions' as Bitcoin breaks $1,000
It was mid-October when a new form of malware quietly found its way onto one of the computers of a small business in England, threatened to permanently encrypt most of its files, and then did just that.
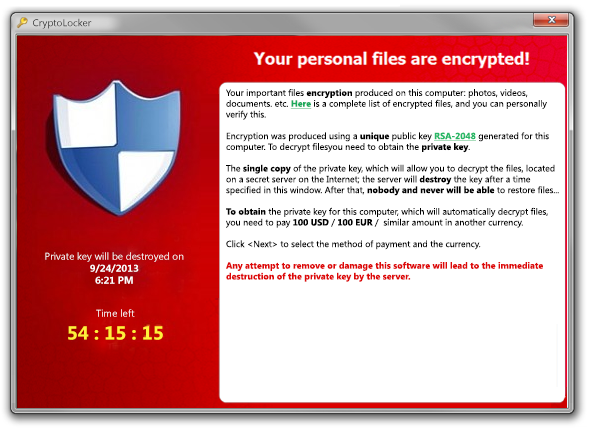
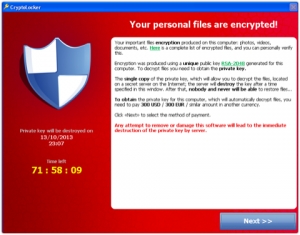
IT administrator David* had never heard of Cryptolocker, and was nonplussed when he got into the office that morning and saw a strange pop-up with a timer that was counting down.
It told him that thousands of his company's files had been encrypted, and that he had to pay a $300 ransom to get the decryption key to save them or else they'd remain locked forever. He had no backups, but he also gave no thought to paying up. David and his company were one of the early victims of Cryptolocker, a type of malware also known as ransomware that has spread via e-mail across thousands of computers in the U.K. and forced people to literally put a value on their data.
"I couldn't understand how the trojan got in and why the antivirus didn't stop it," David says. When he checked his antivirus logs afterwards, he could see when the malware had entered, but there had been no quarantining action and it was left to spread. In the end, Cryptolocker did exactly as it threatened, leaving everything encrypted and the key deleted. The files were not vital and the company could afford to lose them, but it was "a bit of a blow to my pride," David says. "I didn't even think about the payment method because I felt so angry that criminals would benefit from that." He ended up getting rid of the malware by rolling Windows XP to a previous restore point to eliminate the malware, which of course didn't restore the encrypted files.
None of his colleagues would own up to opening the fake, e-mailed attachment that let the malware run loose. Cryptolocker has been spreading via what looks like legitimate business e-mails, fake FedEx and UPS tracking notices, or phony correspondence from banks and other financial institutions. The emails are targeting small businesses, and the malware goes after Windows files (70 different ones) such as PowerPoint and Excel files. If files are shared on a network, the malware can spread to other machines too, or USB thumb drives connected to the infected computer.
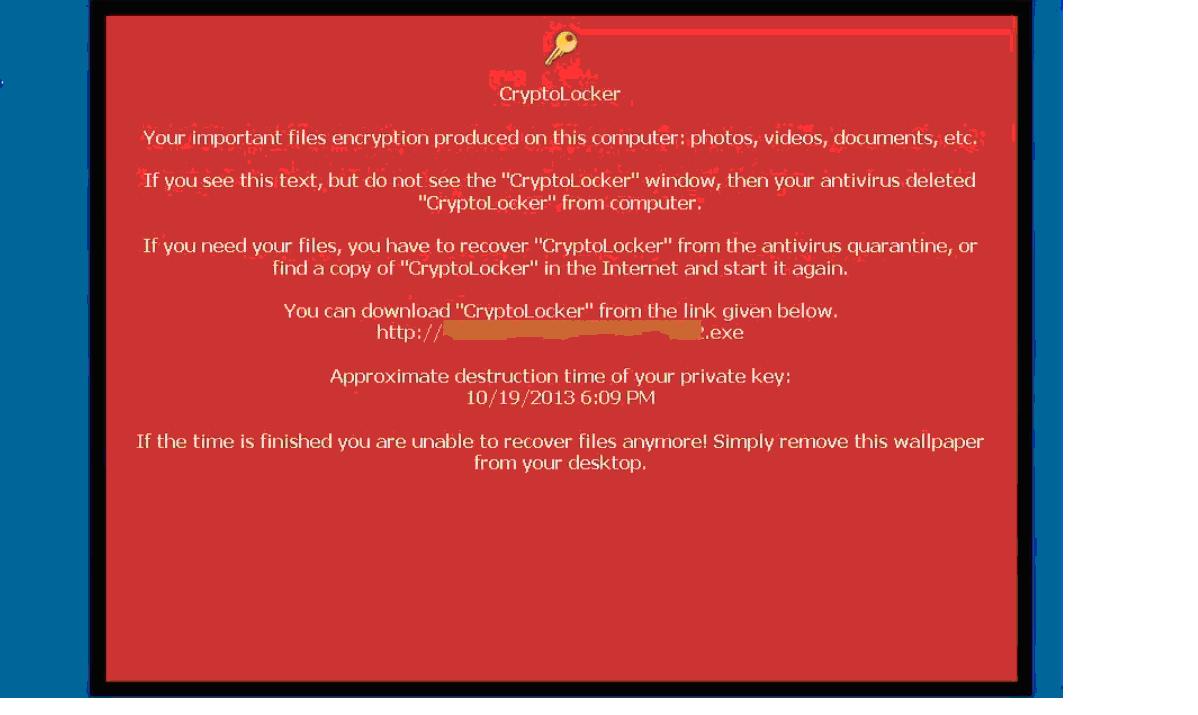
The malware that infected David's company was confined to one PC because it was not networked, and took out .doc, .xls, .pdf and .mdb files. David was willing to pay the ransom but couldn't because they didn't know how to make payments through Bitcoin or Moneypak, which was another form of accepted payment. Earlier this month, the perpetrators changed tack, giving victims a second chance to pay the ransom. The very first ransom demands started at $100, then rose to $300, and are now typically at 2 Bitcoin (roughly $2,000 today).
The second-chance ransom rises five fold to 10 Bitcoin. The controllers even set up a customer service feature on Tor, where victims can more easily pay up. The strange, user-friendly site on the anonymized network says that "customers" simply need to upload one of their encrypted files to get an order number, to then "purchase private key and decrypter for files."Crytolocker RansomWare

